Access management #.ACCESS

Manage access systems centrally, acrossand process-integrated management
#.ACCESS enables the management of online, offline and mechanical locking systems and of course any combination – also with depot systems. Currently, six different systems from various manufacturers in the field of electronic access control can be connected to #.ACCESS.
When it comes to ensuring your company’s security, it’s not just high-quality access systems that are a key issue – but also managing them.
The locking systems of a building ensure full protection only if they are properly managed. Nowadays, however, due to various needs, mechanical locking systems are increasingly combined with electronic systems from different manufacturers.
This fact and many other circumstances, such as espw. a high number of different security zones, a high number of employees, many different access groups and different storage locations for the respective access media mean that secure building management becomes a real challenge! Especially in companies with several thousand accesses per day, it is not easy to control where the individual security zones are located, who has which access authorization and who was given which access medium and when.
The risk that persons who currently do not have access authorization enter the premises increases and thus the security of your company decreases!
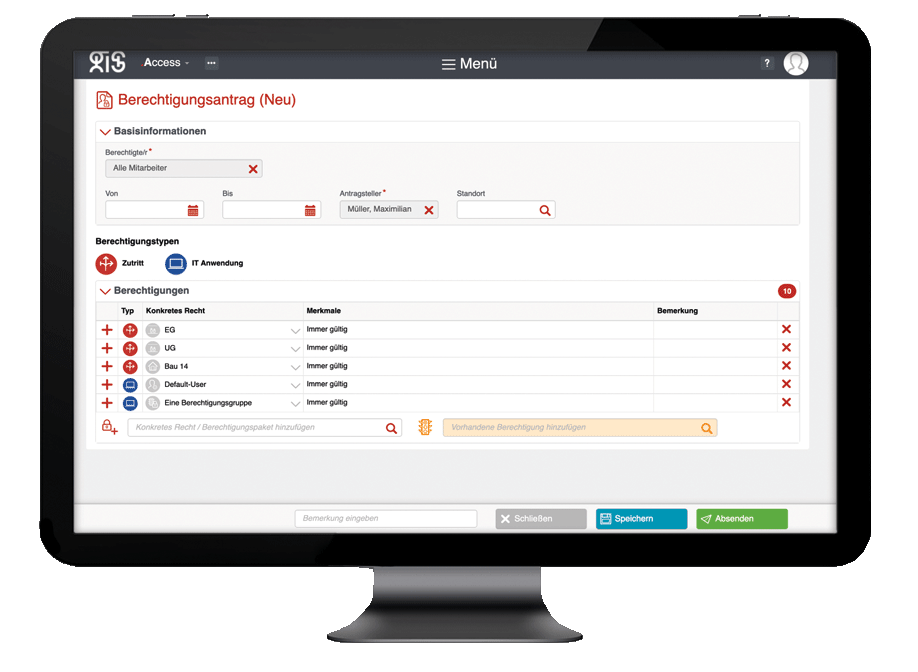
#.ACCESS is the perfect application to manage accesses in a targeted, transparent and secure manner. Accesses are controlled regardless of whether they are electronic, mechatronic or mechanical and regardless of the existing access infrastructure, reading methods or manufacturers.
In the end, this is “only” about mapping the authorization of people to enter a room or not. This is done completely transparently via a clear set of rules and affects all systems and components used equally. When a cylinder from a particular manufacturer is replaced on a door with a biometric component from another manufacturer, rules and processes ensure trouble-free access with the new system components.
The solution for secure management
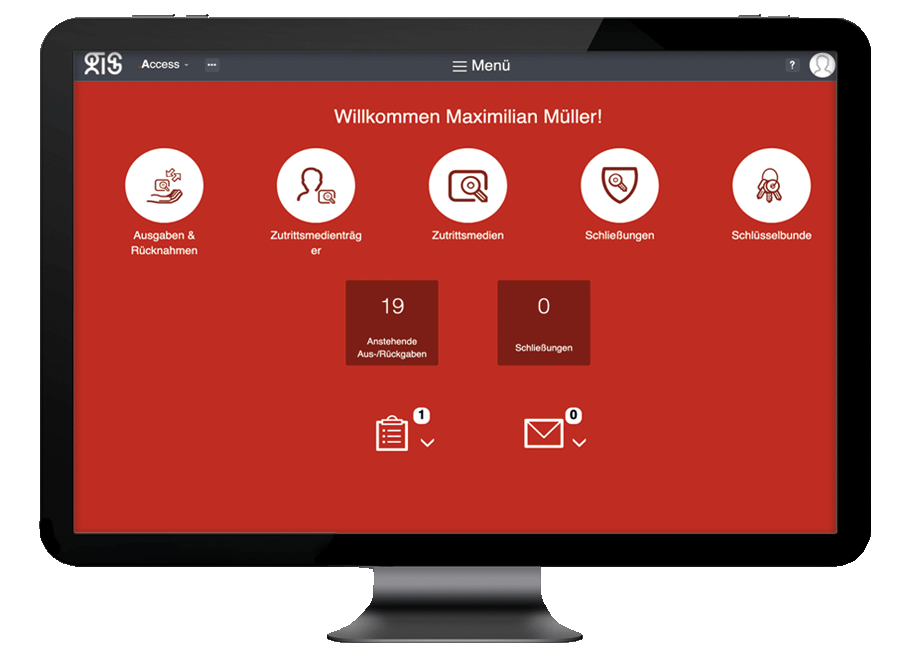
With #.ACCESS, questions like “how many keys are in circulation?”, “has every former employee handed in their access media?” and “where is which security zone?” are history. History! This software solution from gis helps you to manage your company securely.
Cross-manufacturer overview of all required information
#.ACCESS bundles all the information you need on access control as well as access and building management and makes it available to you in a clear and concise manner – regardless of the manufacturer and type of access system.
Flexible adaptation to individual requirements
Due to the modular combinable functions and processes as well as direct or indirect control of 3rd party access technology, you get a lot of leeway to use .secure.ACCESS according to your requirements.
Scalable mapping of your business processes
– Management of different access systems
– ONLINE
– OFFLINE
– KEY (mechanical)
– DEPOT
– All combinations
– Access group management
– Safety zone mapping